Reverse Engineering Remote Control Power Sockets - Part 3: Protocol analysis with SDR
Tooling
Software-defined radio supported by Gqrx (e.g. Noxon DAB Stick)
SDR
In the last blog post Part 2: Protocol analysis with oscilloscope, I used an oscilloscope to record the protocol send by the remote control. This time I'd like to show a cheaper approach to get to the same result. The DVB-T sticks supported by rtl-sdr are able to tune to the 433 MHz UHF band and can be used as a Software-defined radio (SDR). Using free software like Gqrx and Audacity, it's possible to fully reverse engineer the codewords send by the remote control's encoder chip. All needed information is already known from the blog post Part 1: Information gathering.
Record codeword with Gqrx
Gqrx is an excellent, easy to use, open source software defined radio receiver supporting rtl-sdr devices like the Noxon DAB Stick. See the list of Supported hardware to check if your device is supported.
Modulation
Readers interested in radio communication may have already noticed by reading the encoder datasheet, that all circuits showing UHF band data transmitters, implement an amplitude modulation (AM) modulator. The carrier frequency (433.92 MHz) can be found in the power outlet manual or on the remote control's backside.
Gqrx settings
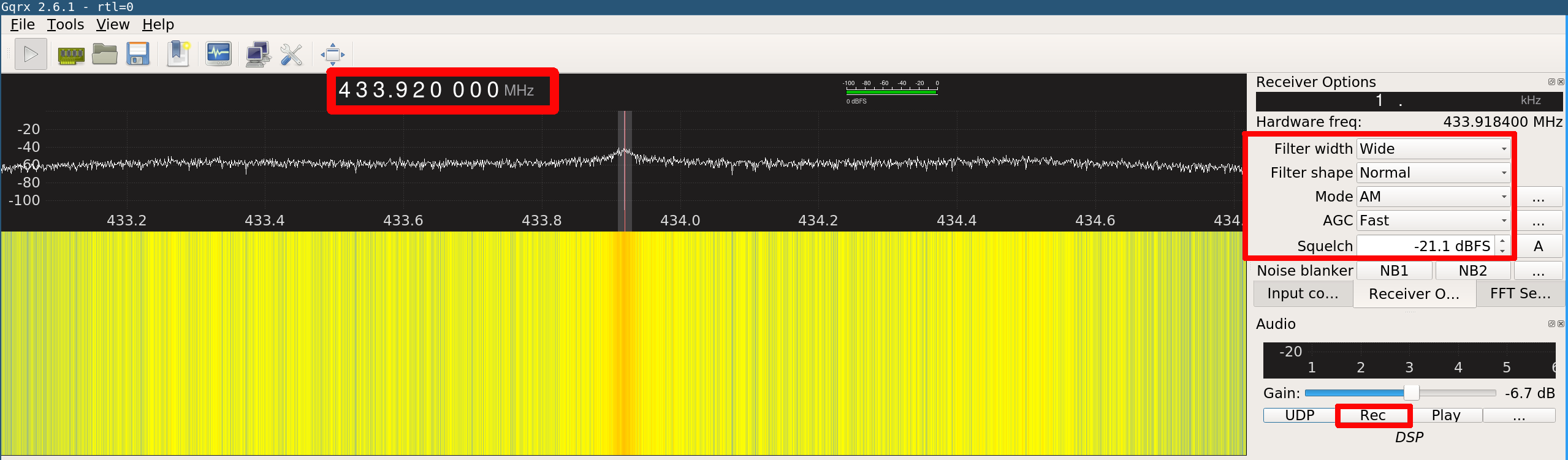
Gqrx can be used to record a complete remote control transmission to a .wav file. The recorded audio file can then be analyzed with Audacity. The output file gets stored to the home folder, the filename looks similar to gqrx_20170422_152940_433920000.wav. This file can now be opened by Audacity for analyzing the codeword.
Analyze codeword with Audacity
Audacity is a free, open source, cross-platform audio software. It can be used to view the demodulated codeword audio files generated by Gqrx.
Outlet group 0 | Outlet 1 | On
The following picture shows the recorded codeword for switching on outlet 1 within outlet group 0.
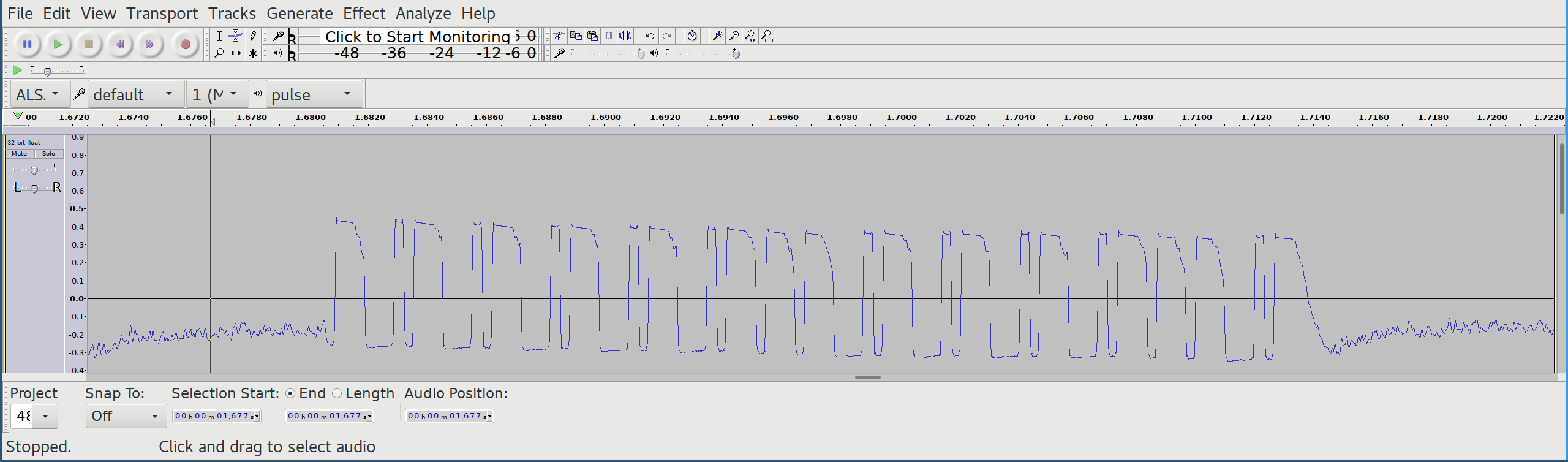
Although the codeword seems to contain valid bit patterns, it is apparent that the first and the last bit (sync bit) look weird. A quick look into the decoder datasheet (PT2272) shows an inverting stage in the RF Application Circuit. Luckily, Audacity offers the possibility to just invert the audio track:
Effect -> Invert
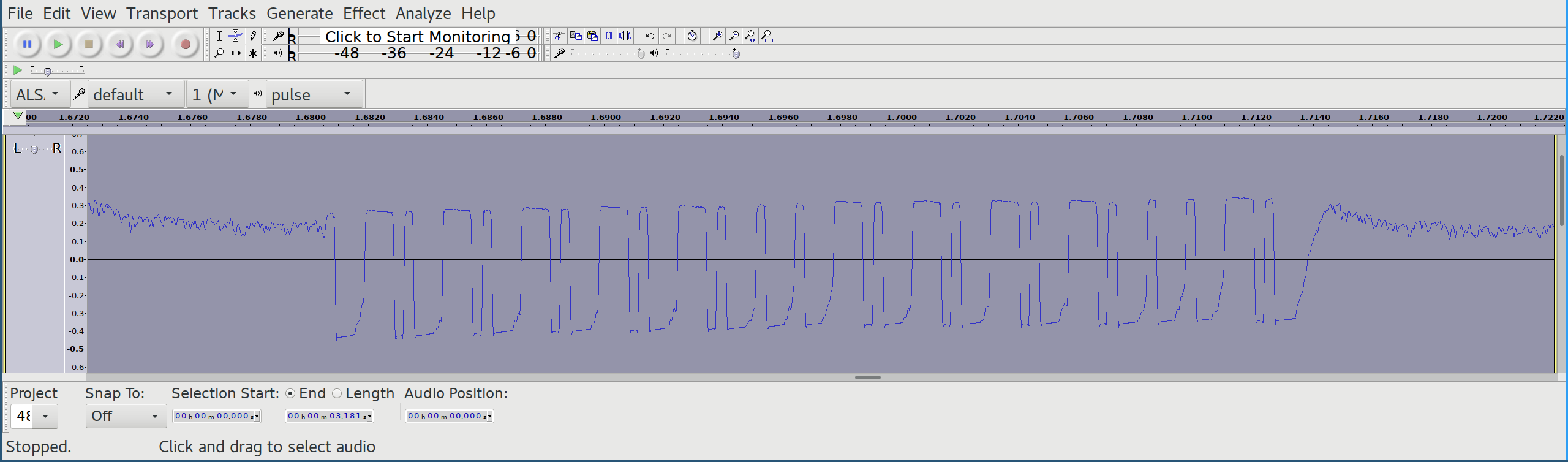
The first bit pattern still looks a little bit weird, but the rest of the codeword matches exactly the result we already know from Part 2: Protocol analysis with oscilloscope.
Group |
Outlet |
On/Off |
|---|---|---|
FFFFF |
0FFFF |
0F |